Antimalware products detect vendor-developed applications for a variety of reasons, usually revolving around their belief that the app is cheating, scaring, or tricking the consumer.
We offer vendor-developed apps a certification service so that a vendor can develop a consumer-respecting app, knowing they won’t be surprised by a detection. Our certification service verifies the app’s behavior, as well as the behavior of its ads, how it distributes, and its purchase, support, and call center methods. We offer a comprehensive, evolving checklist of Application Certification Requirements to help our customers stay compliant. These requirements have been thoroughly vetted over the past six years with many security companies.
Each security company releasing antimalware products maintains their own criteria for detecting vendor-developed applications. Usually these criteria align with our requirements, but sometimes we have differences. We strive to understand these differences by working with the security companies, so we can tell vendors how ensure their apps remain consumer-respecting and not detected.
One way we try to keep in sync with the security companies is by running tests. Every month we produce an Unwanted Software Handling Certification Test (we call it the DeceptorFighters Test for short) Report. In this test, we measure how well various antimalware products can block and allow vendor-developed applications.
To pass the test, an antimalware product needs to get a 95% score on blocking Deceptors and allowing Certified apps. We provide free feeds of all the apps in the test, and we allow the antimalware products to dispute our scores by telling us why their policies led them to allow the Deceptor app to run, or to block the Certified app.
We’ve been running this test for over three years, and we’ve figured out that the security companies behind the antimalware products we test are at various maturity levels for how they handle Unwanted Software (UwS) and Potentially Unwanted Apps (PUA).
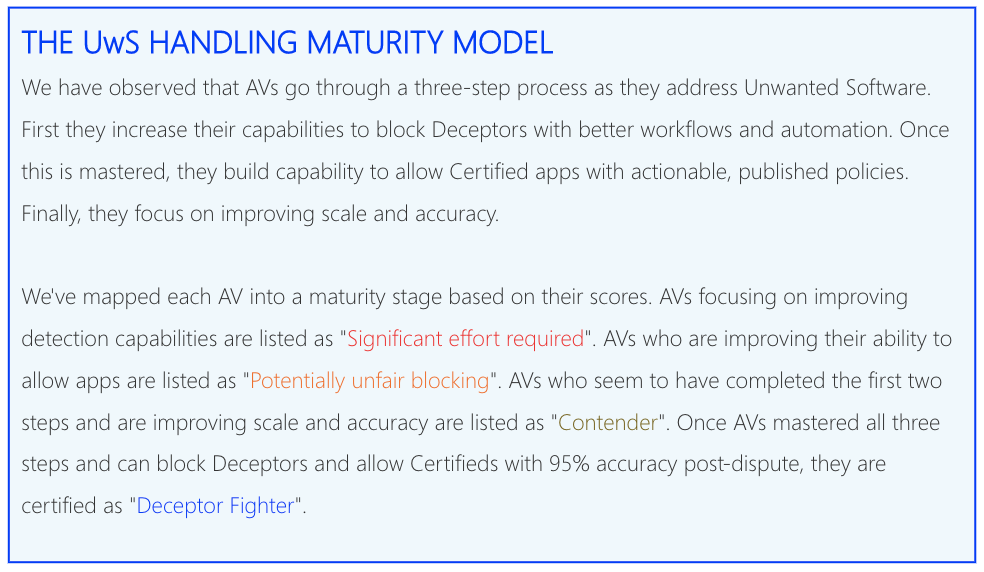
Below we’ve mapped these maturity levels, from most to least mature, into the reasons why an antimalware product may detect a certified app.
DeceptorFighter antimalware products: they generally provide vendors and us with the actionable reasons why they detect Certified apps. They usually have well-published and well-understood policies for vendor-developed apps. They have a large enough staff handling vendor-developed apps to keep up with incoming disputes.
Contender antimalware products: we’ve seen they are actively working to distinguish between wanted and unwanted software. They have researchers dedicated to analyzing vendor-developed applications, and they publish their criteria. They can usually explain why they detect a Certified app, and they generally respond to our queries. We believe the security companies behind them are working on getting more mature in this area, and their antimalware products will soon be DeceptorFighters.
Potentially Unfair Blocking antimalware products: we notice that they claim to be great at detecting UwS and PUA, but ether they haven’t established public criteria for doing so, or they don’t have an efficient way for vendors to dispute these detections. Most of the security companies behind these products don’t communicate well with us, either, leaving vendors in the dark as to why they’re being detected. These security companies may be rewarded for their unfair detections by falsely claiming protection, driving up their own conversions to paid products.
Significant Effort Required antimalware products: we believe that the main reason these security companies detect Certified apps is because they don’t put any focus onto UwS or PUA. They may be great at detecting malware and ransomware, but their abilities to focus on vendor-developed applications is either unfunded or immature.
To think about why a Certified app is detected by an antimalware company, just map the security company into its corresponding maturity category:
- First, it may be that a DeceptorFighter level antimalware product has provided the app its actionable reasons for detection, and the app has decided to not implement the fixes. Note that vendors of Certified apps have committed to fix issues as they are reported by antimalware companies, so if an app is being detected for this reason, the detection usually only lasts a few days.
- Second, it could be that a Contender level antimalware product is still evaluating the app, and it will take some time (up to a few weeks) for them to clear it before they stop detecting it.
- Third, a Potentially Unfair Blocking level antimalware product may be monetizing its detection, or they may have made a conscious decision to ignore disputes from vendors. Note that most of these vendors are small, with limited consumer market share.
- Fourth, a Significant Effort Required antimalware product might have automation-level detection, with nobody monitoring the results.
We suggest that our customers focus on ensuring their Certified apps have no detections by DeceptorFighters and Contenders, because these security companies are mature enough to not only have well-understood policies, but also to have the staff in place to handle vendor disputes. Fortunately, the antimalware companies in these two categories make up the vast majority of the consumer market share.
Here’s a list of antimalware products that remained either DeceporFighters or Contenders for the entirety of last year (see the 2021 report here):
Meanwhile, we continue to try to work with all security companies. Our Deceptor and Certified feeds, as well as our ACRs, are available free of charge for security companies to use as they work to increase their own maturity levels in how they handle vendor-developed apps.